Secure pairing between smartphone and smartwatch based on gait biometrics
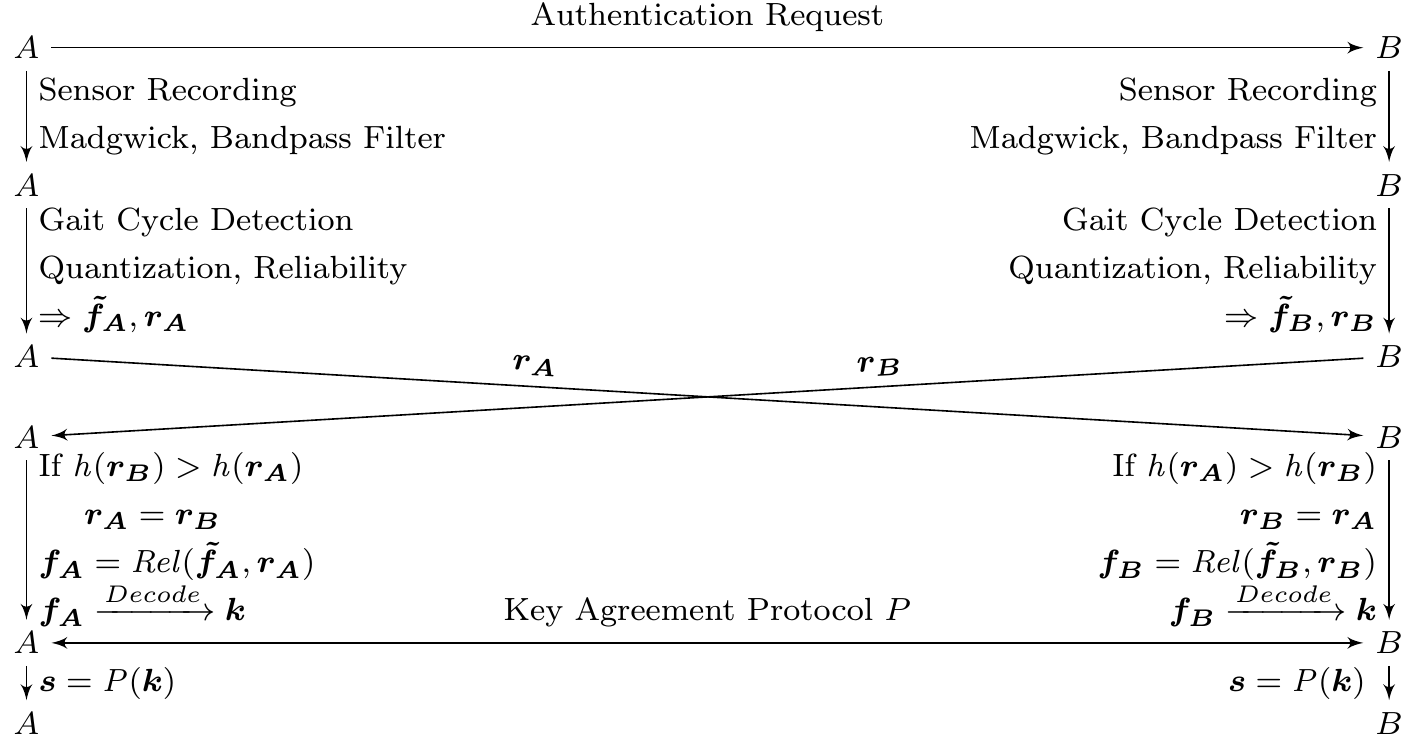
How can we provide secure pairing of devices worn on the same body that does not need any user interaction while still providing protection against active Man-in-the-Middle attacks? Instead of using passwords or numeric comparison, we thought about other secrets which could be obtained on both devices to protect the pairing process. Our idea is to record the user’s gait - the individual unique pattern how someone walks - and use it for authentication.
Bluetooth Security
Bluetooth is the most widely deployed device-to-device communication protocol in use nowadays. It is used for pairing smartphones with smartwatches, smart shoes, smart glasses, and even smart thermometers. While we are sharing more and more private information between these devices, nobody seems to bother asking: Are these connections properly protected against attackers?
Today’s Bluetooth security mechanisms are called “Secure Simple Pairing” and allow for secure pairing via entering passkeys, comparing numbers, out of band verification via NFC, or without any user input (“Just works” profile). Everyone of us has used them, one way or another. All these methods provide protection against passive attackers eavesdropping on the Bluetooth channel during the pairing process. For best usability, the “Just works” profile can be used. It requires no display and thus no user interaction except pressing a pairing button on both devices. Unfortunately, it is not secure against an active Man-in-the-Middle attack, where an attacker is placing herself in the middle of the connection relaying messages between the devices.
Use the Gait!
How can we provide secure pairing of devices worn on the same body that does not need any user interaction while still providing protection against active Man-in-the-Middle attacks? Instead of using passwords or numeric comparison, we thought about other secrets which could be obtained on both devices to protect the pairing process. Our idea is to record the user’s gait - the individual unique pattern how someone walks - and use it for authentication.
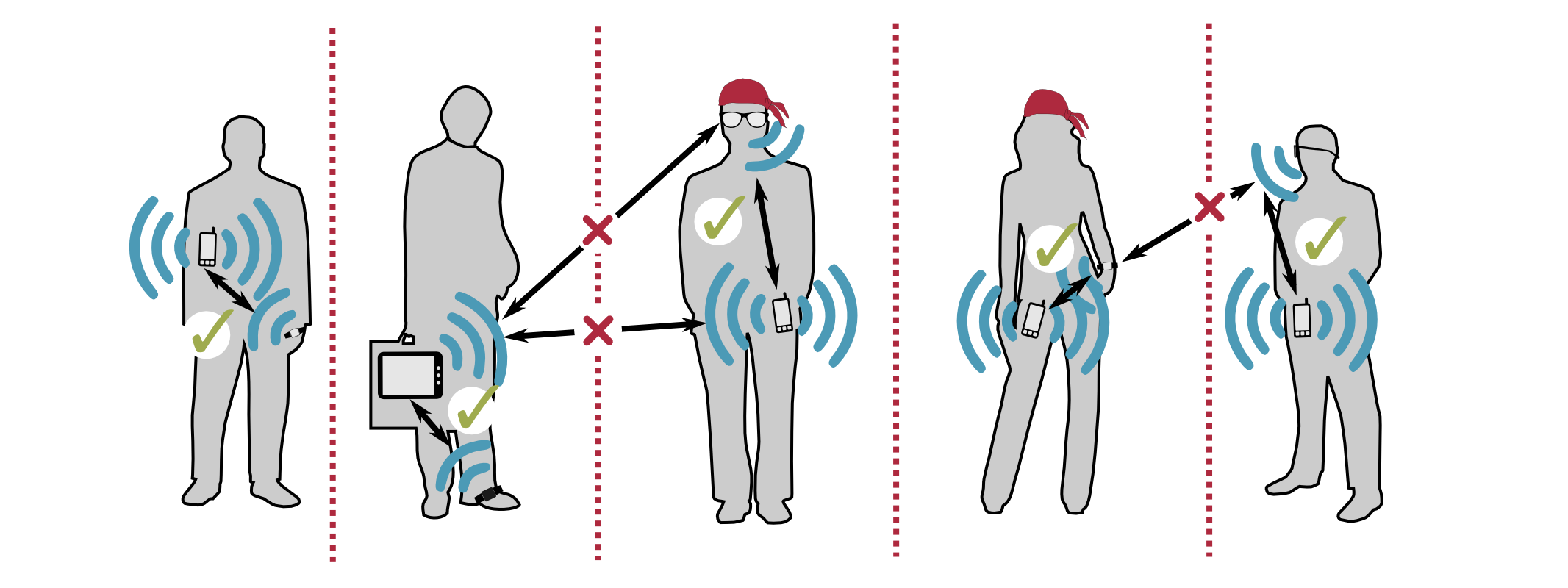
Our hope was, that the gait pattern could be obtained independently of the device’s location on the user’s body. Ideally, a fingerprint generated from accelerometer’s raw data on your forearm (smartwatch) should be the same as the one generated on your waist (smartphone). Thus, your smartphone could now be paired securely with your smartwatch authenticated by a secret fingerprint that is unique to your body and its specific movement at a specific time. In contrast, fingerprints generated on bodies nearby should be sufficiently different to the ones generated on your body. Furthermore, an attacker should not be able to guess your fingerprint by trying out all possible combinations (brute force attack). This creates implicit security barriers between persons as depicted in our scenario:
Signal Coherence
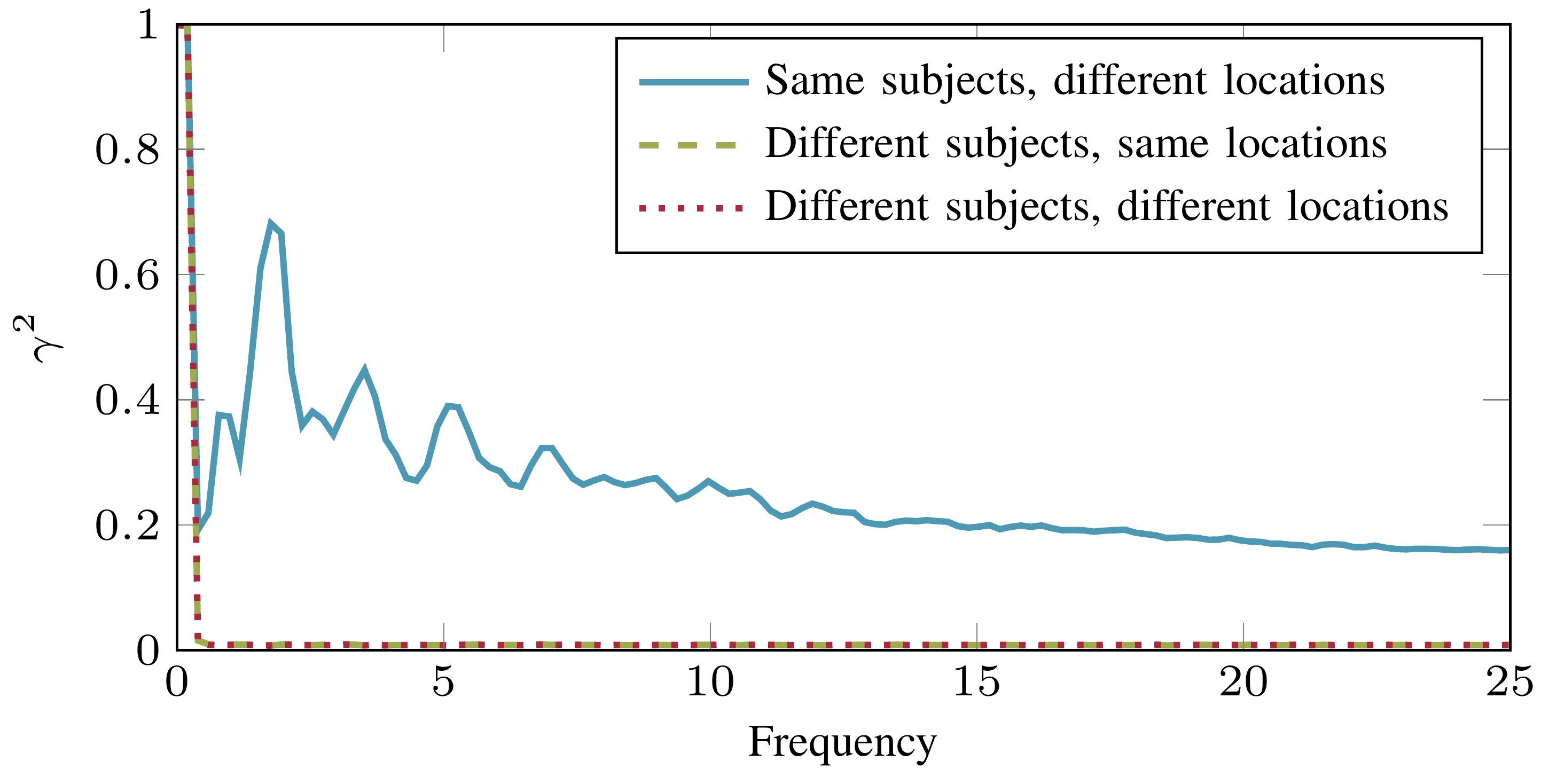
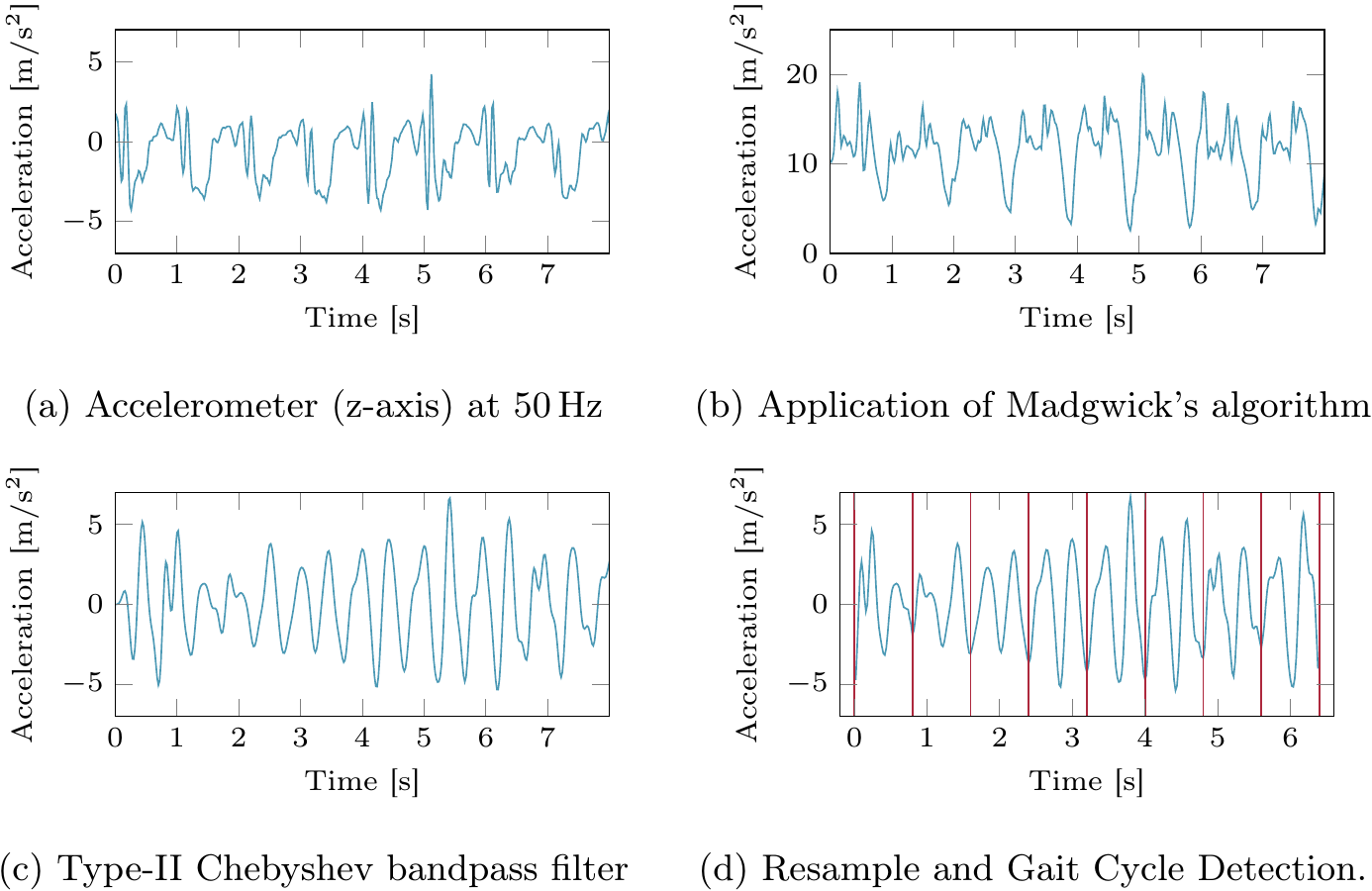
After pre-processing the data to correct the rotation error of accelerometers and applying some signal filtering, we found significant signal coherence between devices on the same body, while devices on different bodies showed no correlation:
Generating Secrets from User’s Gait
For the generation of fingerprints, the recorded accelerometer data is first separated into individual steps using auto correlation:
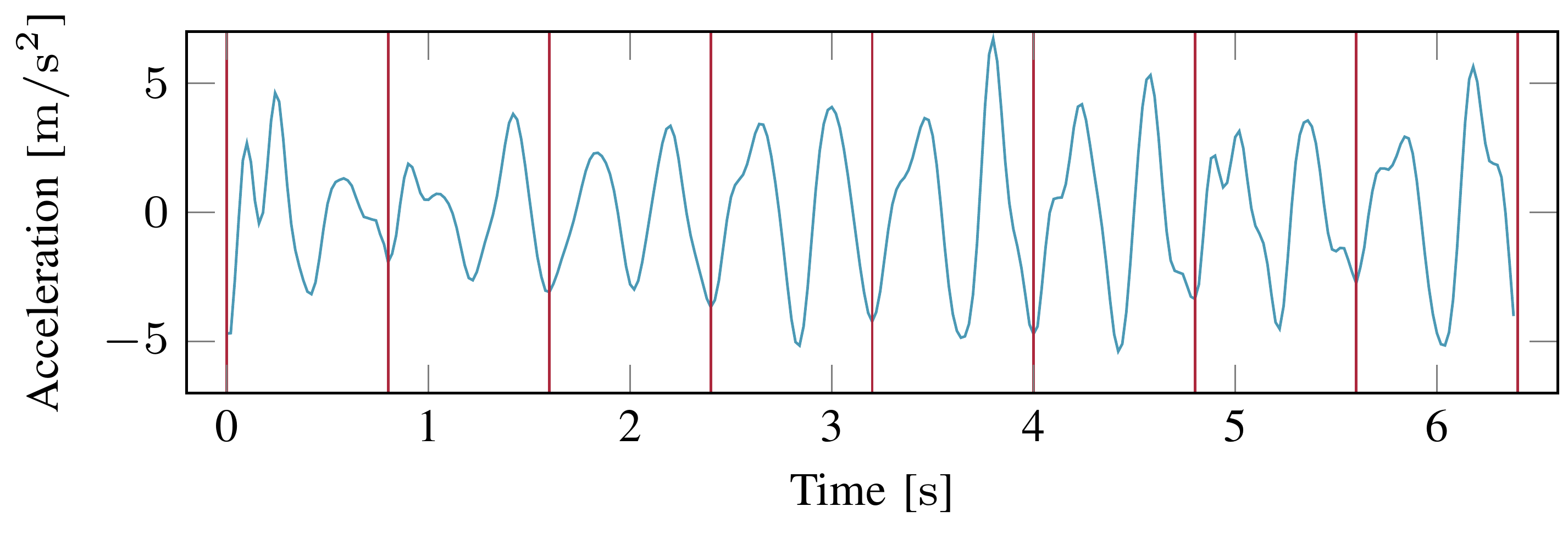
These individual steps are now used to calculate the average step’s acceleration, which is required in the following. The fingerprint is a binary vector generated by looking at the differences between the individual steps in comparison to this calculated average - if the acceleration is higher than the average value on point in the gait cycle, we denote 1, and 0 otherwise. An example is given in the figure below, under a). As can be seen, the acquired fingerprints do not match perfectly. To improve the similarity between fingerprints - remember, these need to be calculated on each device independently - we discard fingerprint bits that are prone to differing. We assume, that bits are more unlikely to flip the greater the difference to the averaged acceleration. In our final specification we generate 192 bit fingerprints and reduce them to 128 bit, disregarding 64 bit.
In the following picture, acceleration values bigger than average are shown as blue, those below as red. The fingerprint derived from these comparison is shown in a), reliability values are in b) (darker blue -> higher reliability). In c), fingerprints are sorted based on the reliability of the forearm and the least reliable bits are thrown away (striked through bits).
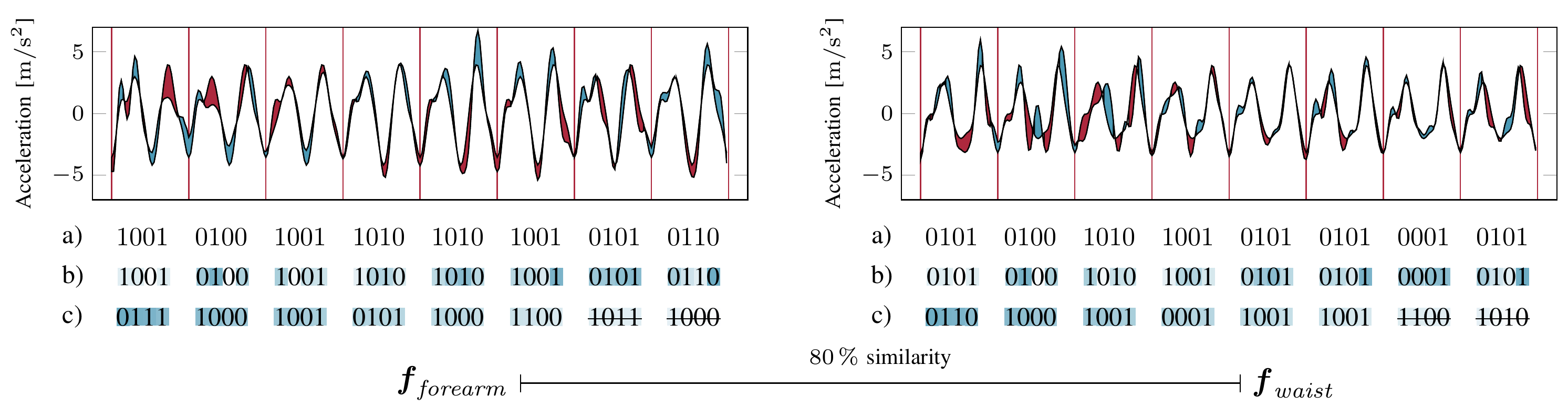
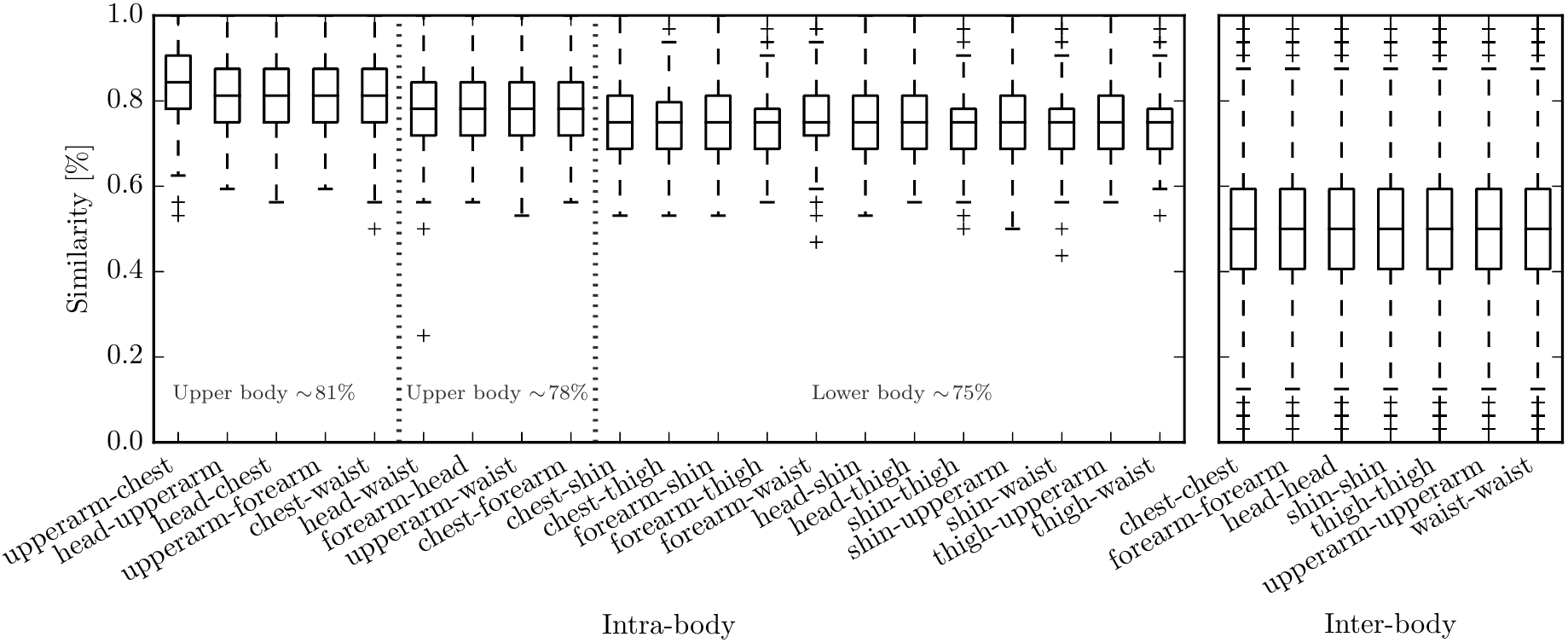
Applying these steps, we get a mean similarity of 82% between fingerprints generated on devices worn on the same body, while similarities between fingerprints generated on different bodies are indistinguishable from random (50%). The details of how we calculated these mean values are explained in our publication.
Fuzzy Extractor
Since we need to achieve perfect similarity between fingerprints, we propose the usage of a Fuzzy Extractor scheme, such as Fuzzy Commitment. The Fuzzy Extractor can be configured to only correct a specific amount of bits, suitable for the chosen bit length and scenario. This accounts for the last 18% of differing bits.
Secure Pairing
Finally, the error-corrected fingerprints can be used as secrets to authenticate the Bluetooth pairing. Our method not only works without any user input, it es even possible to employ periodic re-pairing to dynamically authenticate with new devices attached to a body making it fully interaction-free.
Publications




![paper Moves like Jagger: Exploiting variations in instantaneous gait for spontaneous device pairing [link]](http://bibbase.org/img/filetypes/link.svg)